Is Your Personal Data Safe?

By An Byeong-min, CEO of Openbizlab
[5booninno= An Byeong-min] Protecting personal information is of paramount importance. While innovative security models like Zero Trust are being proposed, individual responsibility and effort remain crucial. Simple everyday practices such as using strong passwords, enabling two-factor authentication, and being wary of suspicious emails and attachments can help safeguard our invaluable personal data.
0. Just Dropped a Smartphone
Na Mi, an ordinary woman in her twenties, drops her phone on the bus while returning home after an outing with friends. The person who finds it, Jun Yeong, secretly installs spyware before returning it. Through the cloned phone, Jun Yeong monitors Na Mi's daily life, learning about her home address, workplace, and her circle of friends. He even ruins her personal relationships via her social media accounts, isolating her. This chilling plot is from the movie “Unlocked”, a film that vividly portrays the dangers of cybercrimes and the anguish of its victims.
 [Image=Netflix]
[Image=Netflix]
1. The Importance of Personal Data in Verifying One's Identity
The digital transformation spurred by advancements like Artificial Intelligence is undeniable. As the world becomes more digital, proving one's identity in the digital realm has become distinct from the analog reality where one's face was enough. This underscores the growing significance of personal information.
Personal data includes identifiers like credit card numbers, social security numbers, phone numbers, addresses, and email addresses. Such information can be exploited in credit card fraud, voice phishing, spam, and more. It might even be illegally sold. The fervor with which hackers pursue this data is evident. They lure individuals into clicking suspicious emails or links to steal personal data and exploit vulnerabilities in corporate or government security systems to extract it.
Imagine if someone had access to the data that verifies “you are you". What if an impersonator roamed the digital world committing various crimes under your identity? What if they targeted your life, your family, or your assets? It's a terrifying thought. The protection of personal data is far from a trivial or simple matter.
2. Zero Trust: never trust, always verify
There is no such thing as a completely trustworthy network, hence the rise of the 'Zero Trust' security model. Zero Trust operates on the principle of trusting no one and nothing. It treats every user and device as a potential threat, demanding thorough authentication and authorization before granting access.
Traditional security models were designed on the assumption that internal users can be trusted. These users could access the network without any distinct verification. But security breaches via internal users increased, often just by obtaining user names and passwords.
The fundamental principles of Zero Trust are:
1. Never trust2. Always verify
3. Least privilege access.
'Multi-factor Authentication' is a cornerstone of Zero Trust. It involves verifying a user's identity using at least two factors – like username and password, one-time password (OTP) sent to mobile phones, biometric data (fingerprints, iris scans, facial recognition), and hardware tokens. For instance, even if a hacker obtains a user's password, they won't have access to the OTP sent to the user's phone, thereby preventing unauthorized access.
Advantages of the Zero Trust model include enhanced protection of personal information, minimized damage from security breaches, and more efficient security operations. Of course, there are downsides – notably, it can complicate the user experience. Nevertheless, the goals of Zero Trust are clear: to strengthen personal data protection and prevent security incidents.
The current state of security can be unnerving. To tackle this, a new technology, the 'OTAC (One-Time Authentication Code),' has emerged. OTAC is a real-time changing single-use code authentication method. It supports both identification and authentication of users and devices, even in offline environments. The method is simple: launch the app, tap an ID card, access card, or payment card to the phone, and a one-time QR code is generated. Inputting or scanning this QR code completes the identification and authentication process.
Although OTAC may seem similar to traditional passwords, unlike static passwords, the authentication code changes every time and can only be used once. Thus, it offers more safety. Even without internet connectivity, OTAC remains convenient.
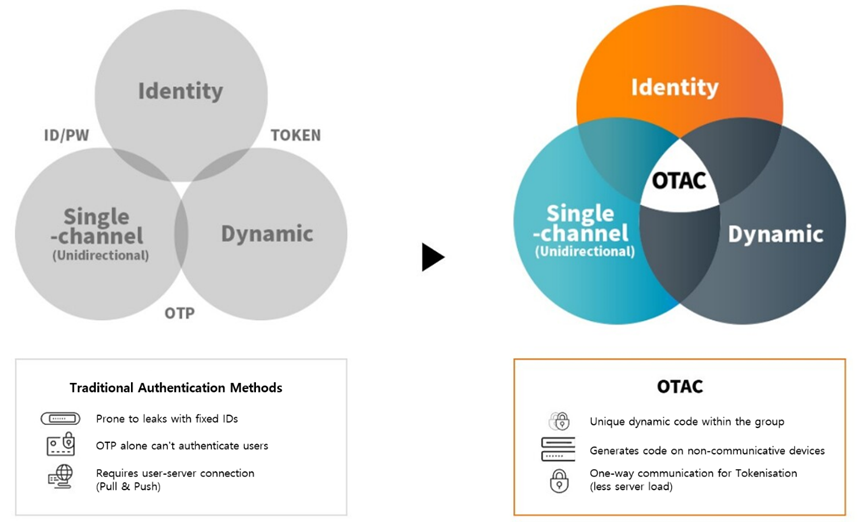
OTAC combines the advantages of the most commonly used authentication systems like username & passwords, code generation, and tokenization. It offers robust security, seamless integration, scalability, flexibility, and cost savings.
Today, with smartphones, we can order food, hail taxis, transfer money, make payments, seal contracts, and trade stocks. It's the digital era where almost anything is possible with usernames and passwords. This convenience demands double or even triple caution regarding personal information security, hence the introduction of revolutionary security models like Zero Trust and OTAC. However, technology alone isn't enough. Personal information security lies in individual responsibility and effort. Scenes from the movie "Unlocked" surpass nightmares, representing unbearable fear. For prevention, a mindset shift and firm guidelines are essential, emphasizing the continuous importance of personal data protection.
Here are some daily practices:
- Use strong passwords comprising at least 12 characters, mixing uppercase, lowercase, numbers, and symbols. Preferably, have different passwords for each service.
- Implement two-factor authentication, a security feature requiring additional verification beyond a password. Services like Google, Daum, and Facebook offer this. It's crucial not to overlook it.
- If you must write down passwords, encrypt them and store them securely.
- Avoid clicking suspicious email links or opening attachments. Hidden spyware can expose your data.
- Refrain from entering personal information on public computers, as they are vulnerable to attacks.
- Understand privacy policies and use personal data protection software.
In the end, you are your best protector. Protecting your personal information starts with you. With awareness, comes change in thoughts, leading to action. Prayers for peace to everyone connecting digitally today. Remember: Never trust, always verify!
ⓒInnovationGuide An Byeong-min

