Without OT Security, Smart Factories Are At Risk
By An Byeong-min, CEO of Openbizlab
In the movie "Blackhat," a sudden explosion devastates a nuclear power plant in China. The root cause is traced back to a mysterious hacker who infiltrated the system with malicious code. The FBI agent in charge of the investigation, Chen Dawai, strongly suspects that the explosion resulted from a cyberterrorist act, but he struggles due to a lack of concrete evidence. On the other hand, Nick, who was once involved in cybercrimes, has completed his sentence and transformed into a formidable cybersecurity expert. Dawai approaches Nick, aiming to conceal his own criminal past, and together they begin to unravel the complexities of the cybercrime case. The movie portrays scenarios where a single line of code can cause a nuclear plant explosion or dramatically surge stock market values, leading to industrial and societal paralysis. Beyond just the film's narrative, real-life instances of cyber-attacks crippling industries are becoming alarmingly frequent, heightening concerns and vigilance in the industrial sector.
Understanding OT Security
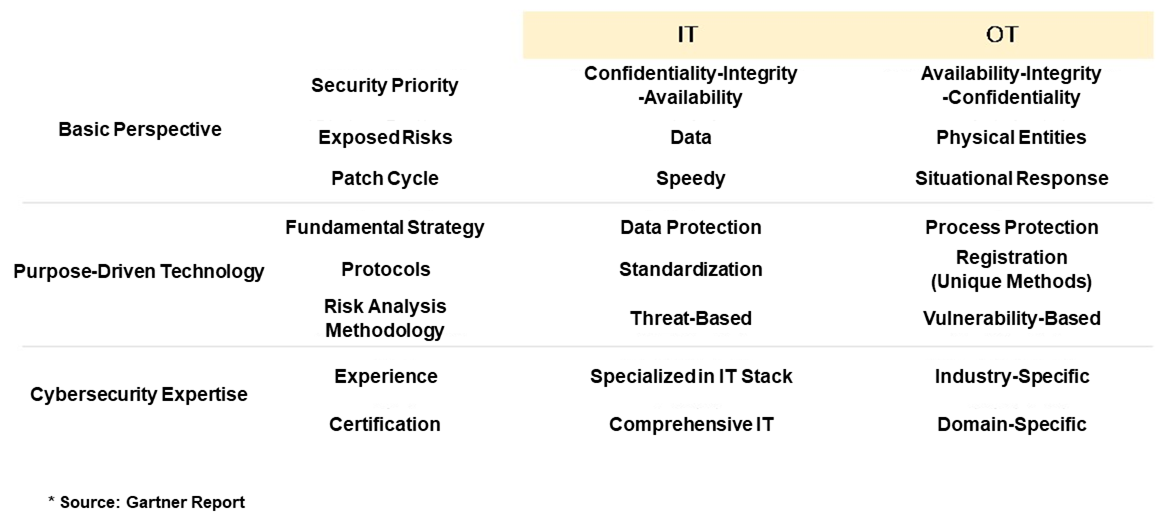
Cyber-attacks on various industrial sectors, such as manufacturing, energy, banking, and transportation, can cause not only operational interruptions but also physical damage. OT (Operational Technology) security is the practice of protecting industrial technology to mitigate such harms. While traditional IT (Information Technology) security mainly focuses on computer networks, OT security broadens its scope to include machinery, manufacturing equipment, and other industrial control systems. The goal of OT security is to enhance the protection of hardware, software, and control systems used in industrial facilities, ensuring that specific industries are safeguarded against external cyber threats.
The Role of OT Security in Smart Factories
Industries are increasingly shifting towards digitization and automation. With the advancements in IT technology, processes within the industrial domain are now utilizing IT solutions to enhance productivity and efficiency. In contrast to traditional manufacturing plants, we now have 'smart factories', which exhibit a higher degree of automation and flexibility. These factories leverage cyber-physical systems, artificial intelligence, and big data analytics to achieve intelligent and optimized production processes.
Take Nike's smart factory, for instance. It capitalizes on digital and automated production techniques to boost its manufacturing output. The factory utilizes automated robotic technology to handle repetitive tasks such as shoe gluing and pattern cutting. Additionally, with the introduction of the 'Nike By You' program, Nike now offers customized production based on individual customer orders – a feat made possible by the infrastructure of the smart factory.
Building a smart factory enables unprecedented levels of automation and flexibility in the production process, maximizing both efficiency and productivity. However, without proper OT security, these smart factories are vulnerable. They face potential threats ranging from cyberattacks and explosions to industrial espionage, all of which can result in significant physical damages and even loss of life.
- Ryuk Ransomware Attack on OT Networks
In the fall of 2019, an attack on U.S. oil and gas smart factories was carried out by the Ryuk ransomware perpetrators. After infecting the organization's IT network, they penetrated the smart factory by monitoring and controlling vital cargo transportation processes and encrypted files. Moreover, they disrupted essential factory monitoring tools, including cameras and physical access control systems. Engineers faced issues such as deleted pages upon logging into their workstations, crippling automated factory operations and forcing manual control for a period. This intrusion not only halted operations but also resulted in a loss of crucial data, leading to damages approximating $30 million.
- Exploiting Vulnerabilities
Hackers often exploit vulnerabilities to gain access to smart factories. According to 'X-Force Incident Response', 89% of OT security network incidents were attacks exploiting these vulnerabilities. Inherently, smart factory systems are connected to numerous devices and networks. A single vulnerability within these numerous connections can expose the entire system to cyber-attacks. A notable incident occurred in 2010 when Germany's Siemens system was paralyzed due to a cyber-attack called Stuxnet. Given that the attack targeted crucial infrastructure, it led to significant industrial losses. This malicious code, which had the potential to damage high-speed rotating machinery and industrial control systems, heightened societal awareness about the importance of securing industrial control systems.
- Information Theft
Attackers also resort to stealthily monitoring or stealing essential information within a smart factory. These hackers might pilfer personal identification information permitted only to authorized engineers or steal the credentials of information administrators to gain access to critical industrial data. Using these illicitly acquired permissions, they could potentially steal sensor data vital for factory automation or the operational process information of equipment. Stored within a smart factory are not only industry secrets but also client data, source codes, algorithms, and operational methodologies. Leaks of such information can expose the company to potential lawsuits from affected clients, regulatory fines, and the operational downtime required for data recovery, casting a severe negative impact on the industry.
Maintaining OT Security in Smart Factories
There's a significant risk associated with Operational Technology (OT) security breaches. Many of the potential accident scenarios are based on real events that have occurred, highlighting the looming danger. Regardless of the advancements in smart factory technologies and the substantial investments to boost productivity, if OT security is neglected, it's akin to pouring water into a sieve – the efforts become futile. So, how can we effectively safeguard OT within smart factories?
- Network Segmentation
By segmenting networks, the potential damage from an attack can be minimized. Vital assets within the network can be quickly isolated, and firewalls can provide real-time screening for potential malware or suspicious traffic, enforcing access control. Creating an "Air Gap" network involves physically separating the network. If budget and operational constraints allow, building an independent air-gapped network within a single system is a viable solution. Alternatively, dividing the network layers can be effective. This approach utilizes existing infrastructure and implements virtual networks, ensuring security is bolstered by the very separation of these networks.
- Access Control
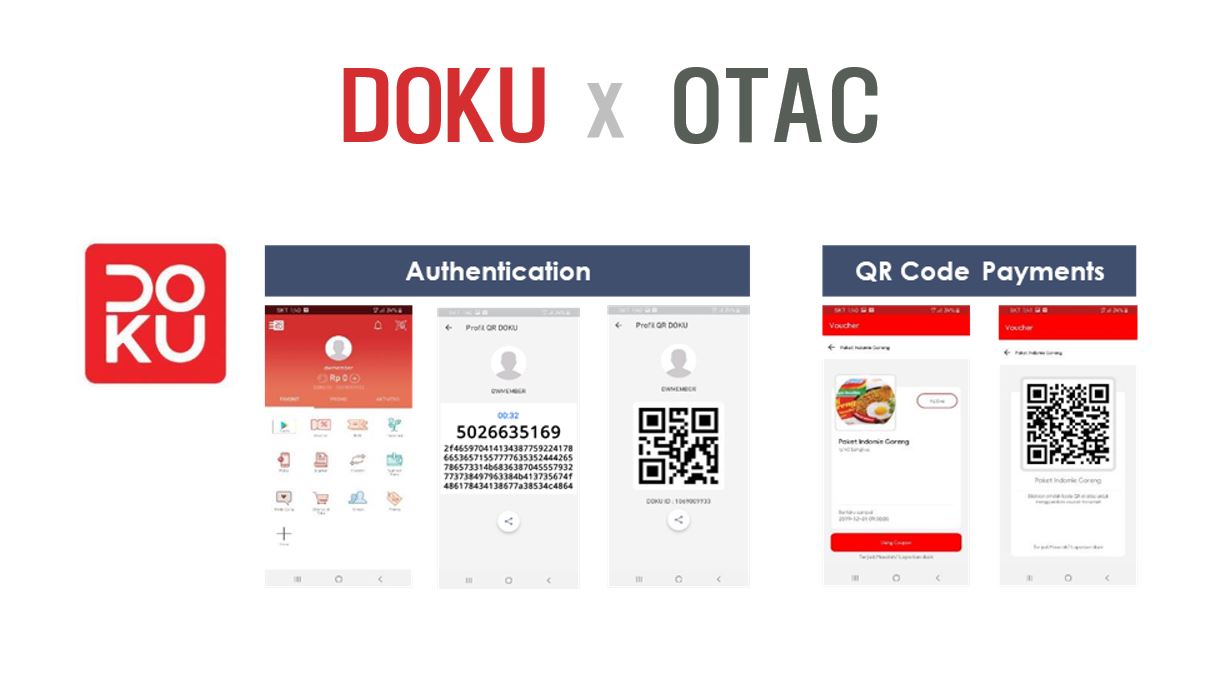
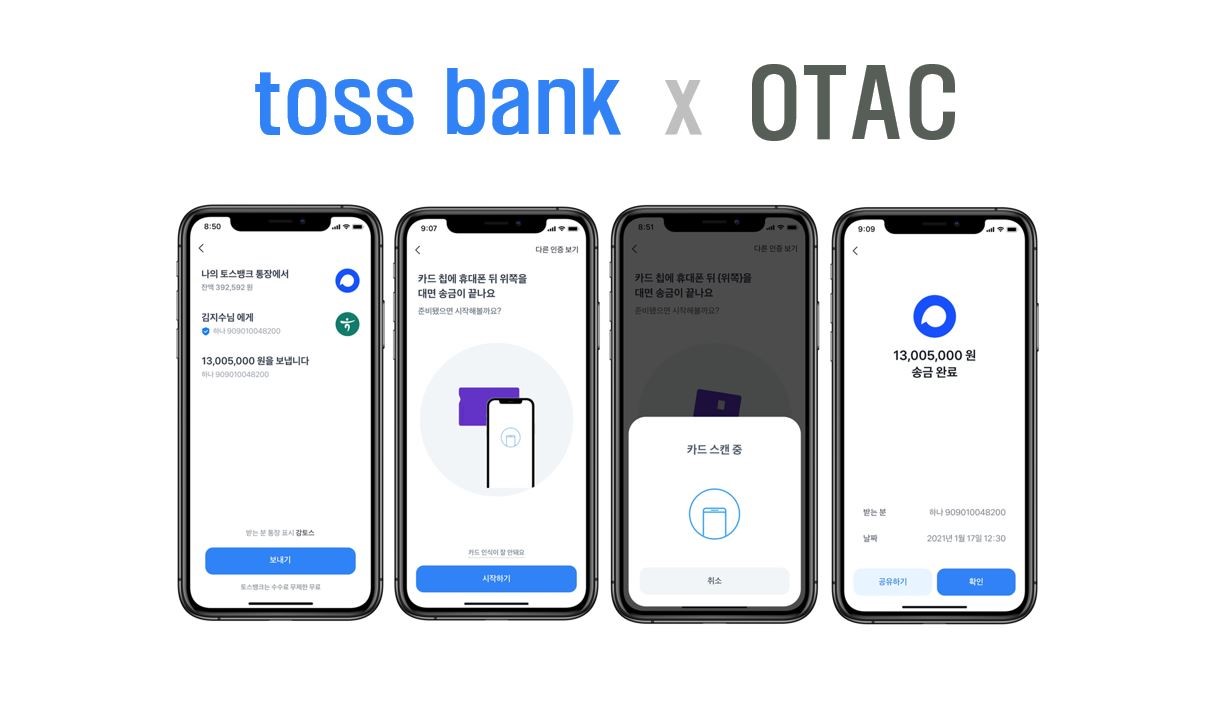
For anyone to access the systems of a smart factory, there must be proper authentication and permissions granted. Employing multi-factor authentication or strengthening controls against unauthorized users can prevent breaches. One method is using One-Time Authentication Codes (OTAC), a solution that doesn't require changing the existing authentication processes or infrastructure. Real-time management of MAC addresses and communication ports can prevent unauthorized access. Continuously updating the access list and controlling protocol access is essential.
- Managing Vulnerabilities
To effectively manage system vulnerabilities, it's crucial to regularly apply security patches and updates. Manufacturers should not only anticipate vulnerabilities but also periodically check for vulnerability information provided by vendors, responding promptly to critical updates. By examining the vulnerabilities of inspected systems and tracking vulnerability trends over specific periods, the root causes can be identified, and solutions can be deployed. This proactive approach can prevent potential OT security incidents.
Additionally, providing security training to employees involved in smart factories is essential to elevate their awareness of potential threats. Regularly communicating the company's security policies and procedures can instill a heightened sense of caution. By informing them of various external attack cases and giving pre-emptive warnings against potential pitfalls, you can foster a vigilant attitude towards OT security within the smart factory environment.
Only two years ago, institutions like the Korea Atomic Energy Research Institute and Korea Aerospace Industries experienced hacking incidents. These breaches led to the leakage of over 40,000 internal documents, including around 60 critical military secrets related to submarines. Even the nation's most secure documents, believed to be impervious to threats, were compromised. As industrial environments continue to converge with IT and become increasingly interconnected, it's a pivotal moment to focus on OT security. OT security requires more than a one-time effort; it demands continuous attention and preventative measures. Given that the consequences in the OT environment can be more severe than in IT, leading even to societal problems, it's time for a proactive and thoughtful approach to OT security.