OT/PLC Security Emerging in the Age of Intelligence and Automation
Damages Caused by Hacking of Operational Technology (OT)
On May 7, 2021, Colonial Pipeline, the largest oil pipeline operator in the United States, was hacked, resulting in an operational shutdown. The impact was enormous, causing fuel supply disruptions in the eastern US, and 18 states declared a state of emergency. Fuel prices rose, and businesses relying on this fuel were thrown into chaos. Eventually, Colonial Pipeline paid the hackers approximately 5.6 billion won in Bitcoin.
In 2022, South Staffordshire PLC, which manages water facilities in the UK, became a social issue after being hit by a ransomware attack. This company supplies water to 1.6 million people daily, and had the water supply been interrupted or the devices controlling the pressure in the water system manipulated, the drinking water could have turned into poison. In early February 2021, a water treatment facility in Oldsmar, Florida, was cyber-attacked, increasing the concentration of sodium hydroxide in the drinking water by more than 100 times. Fortunately, the operator of the water treatment facility blocked the hacker's remote access, preventing a disaster. The security of critical infrastructure is vital for societal safety and cannot be overstated.
As public facilities and companies' factories and operational systems become automated and internet-connected, the importance of OT (Operational Technology) has become more pronounced. OT is a system that controls and monitors physical devices and plays a crucial role in various industries such as manufacturing, energy, and transportation. As these OT environments become digitized, security threats also increase. We will examine the importance of OT security, related considerations, countermeasures, and the impact of generative AI advancements on OT security.
The Importance of OT Security
Imagine how terrible it would be if your computer or smartphone were hacked, allowing someone to access your personal information, financial services, and social media to steal money and deceive your acquaintances. If this is the case with personal devices, the repercussions of security breaches in systems used by companies and public institutions are even more horrifying. This issue began to emerge seriously in the 2000s as the spread of internet connections became standard in information systems. Since the 1960s, large factories and industrial sites have applied PLC (Programmable Logic Controller) and DCS (Distributed Control System) to increase production process efficiency. At that time, security issues were limited to physical access, as these information systems operated without internet connections. From the 1980s, as IT systems advanced, operational technologies of companies began to integrate with these information systems. However, OT security was still not a focus."
However, since 2000, OT security threats have become visible. As internet connectivity became widespread, OT systems also connected to networks, and from 2010, OT security threats began to emerge in earnest. Malicious code attacks targeting national power grids, nuclear power plants, and nuclear facilities became more prevalent, highlighting the need for OT security. During this process, the adoption of cloud technology, factory automation, and smart factory technology accelerated, making OT security an essential consideration for governments and businesses. IT hacking can lead to data breaches, system damage, business interruptions, loss of customer trust, and financial losses. In contrast, OT hacking can cause system shutdowns, physical equipment damage, and even casualties, leading to factory shutdowns, and in severe cases, explosions, fires, and wars.

@ Image by Mohamed Hassan from Pixabay
Countermeasures for OT Security
Over the past few decades, the digitalization of OT environments has been extensively advanced to maximize productivity and efficiency. In the process, the damages from OT hacking have increased, and the need for OT security to defend against these threats has grown. Now, OT security is a crucial issue directly linked to the survival of nations, societies, and businesses. What specific measures can be taken for OT security?
Since OT systems consist of equipment that can be physically accessed, physical security is very important. Strict access control and monitoring systems are needed to prevent unauthorized access. Next, to defend OT systems that are increasingly connected to networks from hacking, network security measures such as network segmentation, firewall configuration, and Intrusion Detection Systems (IDS) are important. Additionally, the OT environment is connected to various suppliers, solution providers, and distribution networks, exposing it to security threats through these stakeholders. Therefore, it is essential to regularly check the security status of these various connected partners and open OT only to trusted entities.

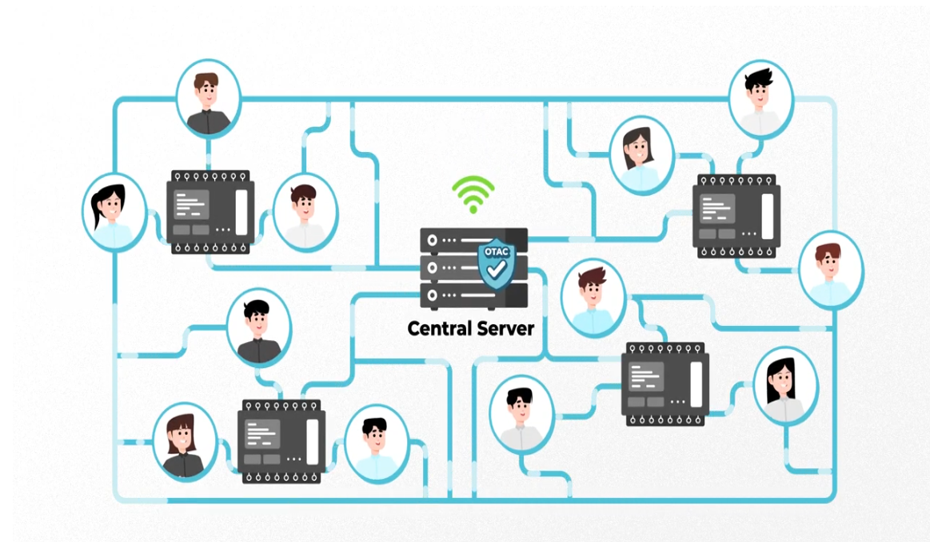
To enhance the security of the OT environment, it is important to regularly update software and adopt the latest security technologies. For example, SSenStone's OTAC (One-Time Authentication Code) is useful for protecting user accounts with dynamic authentication methods. Recently, OTAC has been applied to PLCs, providing security solutions in collaboration with major related companies such as LS Electric and Phoenix Contact. By introducing advanced OT security solutions equipped with the latest technologies, security issues can be proactively addressed. This means that security should be thoroughly enforced before hacking attempts occur, rather than fixing the barn after losing the cow. Text, Screenshot, Photo with Circle Indicated
The Outlook for Generative AI and OT Security
The development of generative AI technology, spurred by ChatGPT since 2023, presents new challenges and opportunities for OT security. Generative AI can be used for data analysis, anomaly detection, and predictive analytics, thereby strengthening OT security. AI can monitor unexpected abnormal activities in real-time, without human intervention or pre-defined rule-based filtering. This provides higher accuracy than traditional signature-based detection methods. Moreover, AI can predict the state of equipment to detect issues in advance and perform maintenance, preventing security incidents.
The new characteristic of OT security brought by AI is automated response. In the event of an unforeseen cyber attack on OT, predicting the resulting damage is challenging. Due to the difficulty in predicting damage, preparing a response plan takes time, and incorrect responses can lead to secondary collateral damage. AI helps in promptly and swiftly responding to the damage caused by an attack.
As such, OT security is becoming increasingly important in the era of digital transformation. Companies must prepare security measures from various aspects, including physical security, network security, vulnerability management, and supply chain security. Additionally, companies should explore ways to enhance OT security by adopting new technologies such as generative AI. OT security will continue to evolve, enabling companies to secure their survival and competitiveness.