PLC OTAC Solution for Safely Protecting OT Vulnerabilities
With the surge in cyberattacks targeting Operational Technology (OT) vulnerabilities in 2023, the demand for OT security technology has been increasing. Here, Operational Technology refers to the technology and systems designed for production automation tailored to various industries, from manufacturing plants, ships, and automotive fields to energy facilities such as water and power. In other words, it is utilized in most areas of our daily lives, not limited to specific industries.
In the past, OT operated in a closed network format, physically isolated, making cyberattacks difficult. However, with the progression of the Fourth Industrial Revolution, IoT technology has been integrated for convenience, efficiency, and productivity enhancement, connecting OT networks to the internet, and consequently exposing them to cyber threats.
In December 2023, for instance, 70% of Iran's gas stations experienced shutdowns due to PLC issues. It was nothing but a software problem at the gas stations, and a hacking group affiliated with Israel boasted on social media about attacking Iran's oil system. This group had previously carried out cyberattacks on Iran's steel company, drawing attention to such issues.
Even simple information leakage can severely impact a company's image. Beyond that, there are potential problems that could cause serious harm to society, such as large-scale power outages, leakage of hazardous materials through terrorism targeting chemical plants or nuclear facilities, electromagnetic interference with railway and aviation communication systems, and so on.

At the end of 2023, Through the hacking group affiliated with Israel, known as "Predatory Sparrow," an attack was launched on the oil pump systems throughout Iran at the end of 2023. As a result, nearly 70% of the approximately 33,000 gas stations across Iran had their operations halted, the Islamic Revolutionary Guard Corps (IRGC) is designated as a terrorist organization by several countries, including the United States, several critical infrastructure facilities, including those in Florida, were targeted in attacks aimed at exploiting vulnerabilities in the programmable logic controllers (PLCs) manufactured by Unitronics, an Israeli automation solutions company, linked to the Islamic Revolutionary Guard Corps (IRGC) through CyberA3ngers.
Furthermore, there have been instances where military facilities, fleets, fighter jets, missile manufacturing plants, and the like have been compromised. Even before the widespread integration of Internet of Things (IoT) technology, various incidents have occurred, such as the power outage in Ukraine, the tram derailment in Poland, and attempts to manipulate the concentration of sodium hydroxide in the United States. As such, there is a potential for even larger issues to arise in the future. Therefore, it is essential to exercise vigilance and implement security measures preemptively.

@ Unsplash-Proxyclick Visitor Management System
In the Operational Technology (OT) domain, vulnerabilities often arise in Programmable Logic Controllers (PLCs), which are core devices used for integrated operation and control. Many institutions and companies access these devices through a fixed-value-based user authentication process, using IDs and passwords. Furthermore, unauthorized access points abound, as IDs and passwords are still commonly recorded on PCs using notepads or Post-it notes.
Writing down IDs and passwords on notepads or Post-it notes is a practice that can be easily improved upon. However, it's a challenging task to completely prevent unauthorized access through hacking and similar means.

Ultimately, the solution lies in the adoption of Multi-Factor Authentication (MFA) systems that can fundamentally block unauthorized user access. However, it is often difficult to apply such systems with existing infrastructure such as hardware and network equipment, and the cost of replacement is significant, resulting in very few cases actually being implemented in practice.
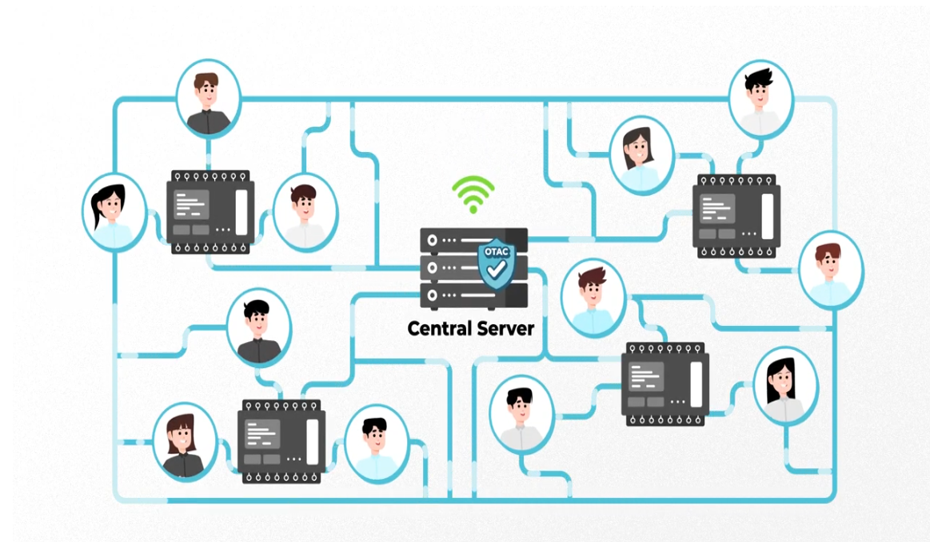
Nevertheless, incidents continue to occur, and the underlying issues are even greater. Therefore, a solution is ultimately needed. SSenStone has introduced the PLC OTAC solution, taking into account these practical aspects. It allows for authentication process enhancement without the need for a separate token infrastructure, while maintaining almost the same hardware and network environment.
This solution utilizes a one-way dynamic token authentication process, rather than the traditional bidirectional dynamic token authentication process, allowing it to be used freely even in closed networks where only one-way communication is permitted.
Furthermore, there is no need for hardware replacement or network environment upgrades, and the existing user experience can be maintained while enabling authentication with dynamic values, eliminating the need for additional training or adaptation periods.
As the issue of OT security vulnerabilities has become a global concern, measures to address them have become essential not only for societal safety but also for the trust of businesses and institutions. SSenStone's PLC OTAC can be introduced in various fields and is an attractive solution that allows for the utilization of existing infrastructure, contributing to safety and trust. Therefore, considering its adoption for safety and trust is worth considering.